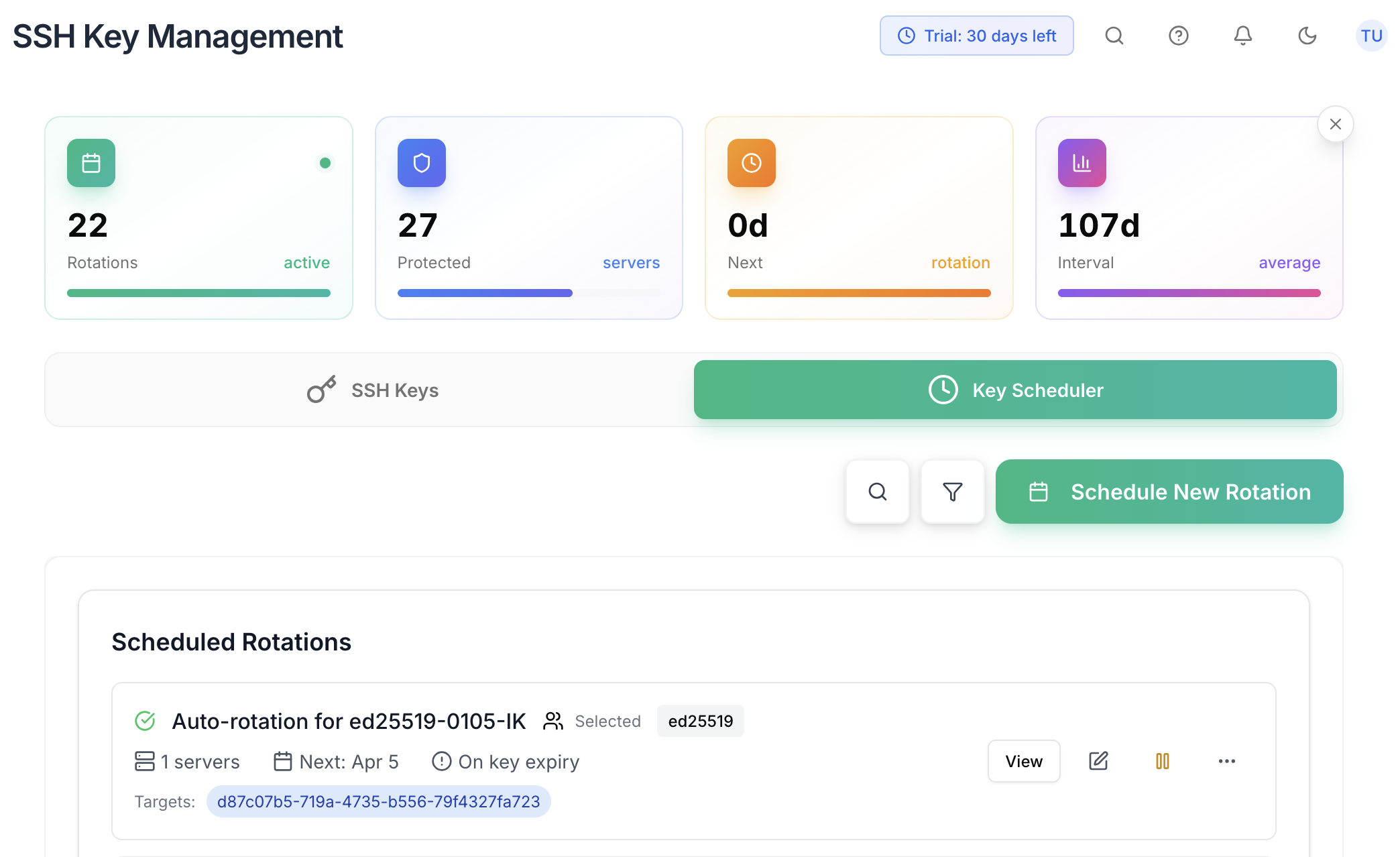
Generate Once, Secure Forever
Set your key rotation schedule and let LinShield handle the rest. Your servers stay secure automatically.
- Flexible Duration - 30, 90, 180 days, 1 year, or never
- Auto-Rotate - New keys deployed 7 days before expiry
- Smart Targeting - All servers, specific, or by tags
- Pre-Testing - Keys verified before replacing old ones
- Auto Backup - Old keys saved before rotation