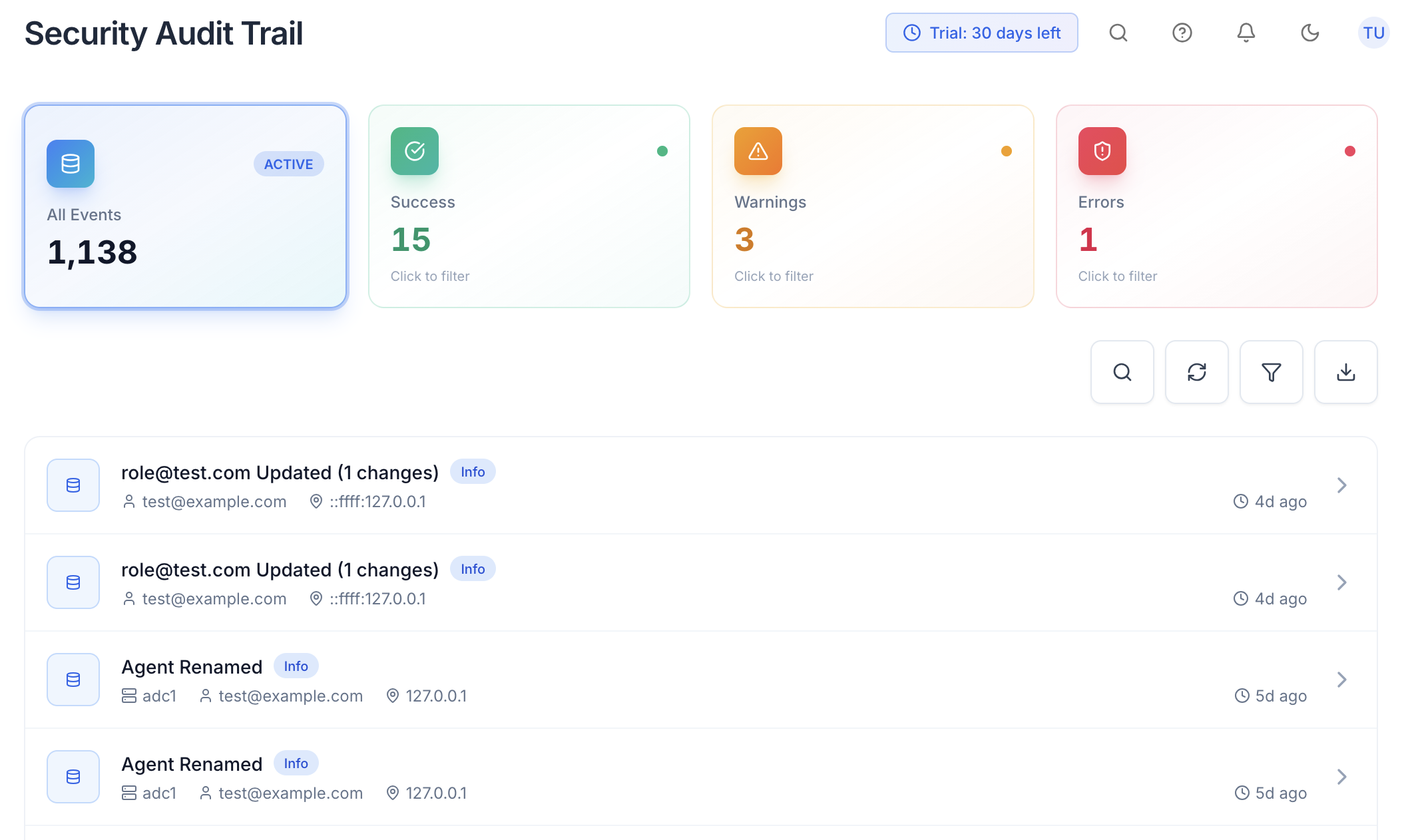
Powerful Log Analysis
- Immutable Logs - Tamper-proof with hash chain
- Real-Time Streaming - See events as they happen
- Actor Attribution - Know exactly who did what
- IP Tracking - Track where actions originated
- State Tracking - Full before/after diffs
- CSV & PDF Export - Download formatted reports