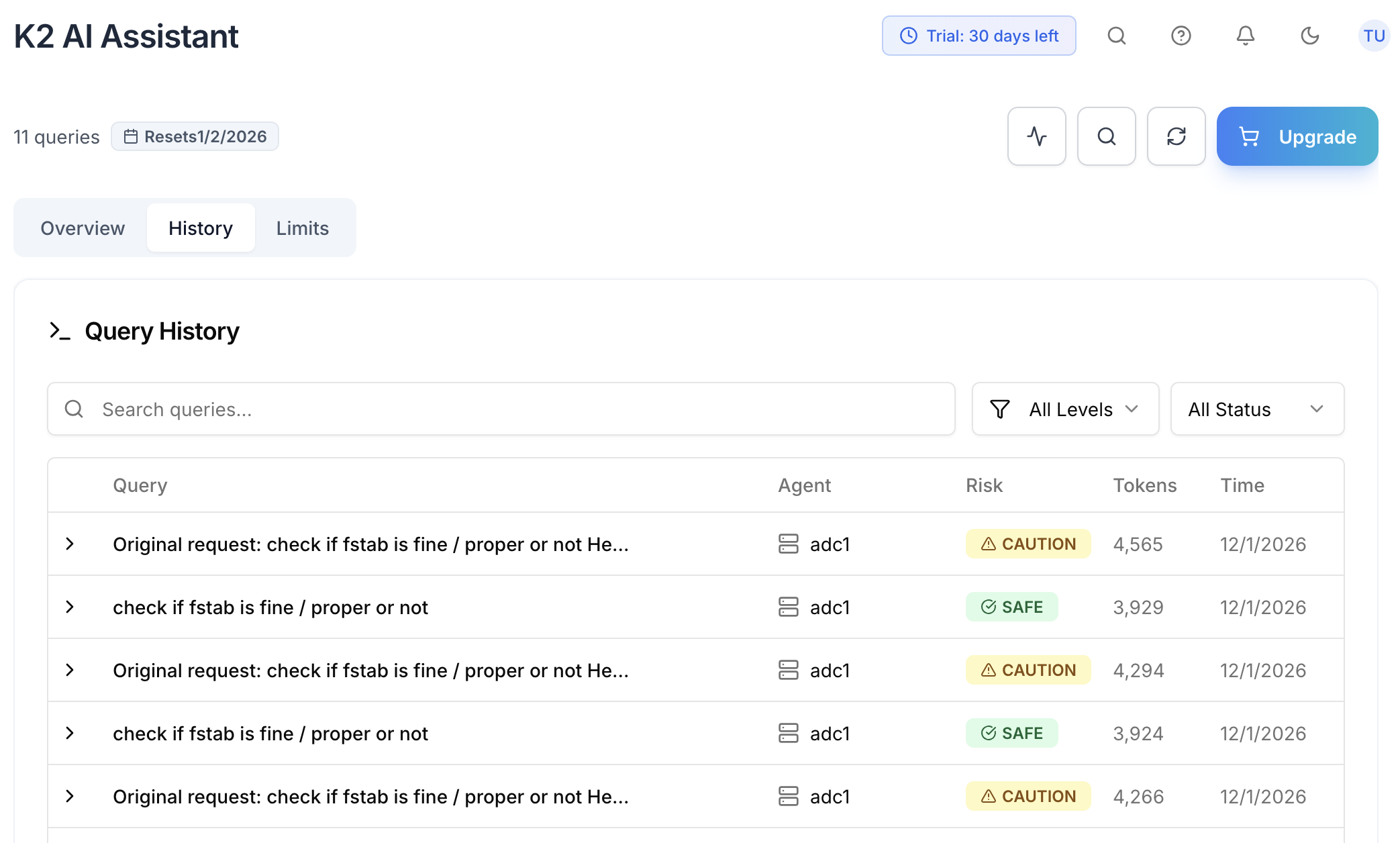
Full Audit Trail
Every K2 interaction is logged for compliance and security review.
- Query Logging - Full text of every question and response
- Token Usage - Track AI resource consumption and costs
- Security Blocks - Log of all blocked dangerous requests
- Agent Context - Hostname, OS, IPs for each query
- Compliance Ready - SOC 2, GDPR, ISO 27001 compatible