Secure Your Linux
Infrastructure
Take complete control of your Linux servers. Manage access, monitor activity, deploy software, and stay compliant - all from one intuitive dashboard.
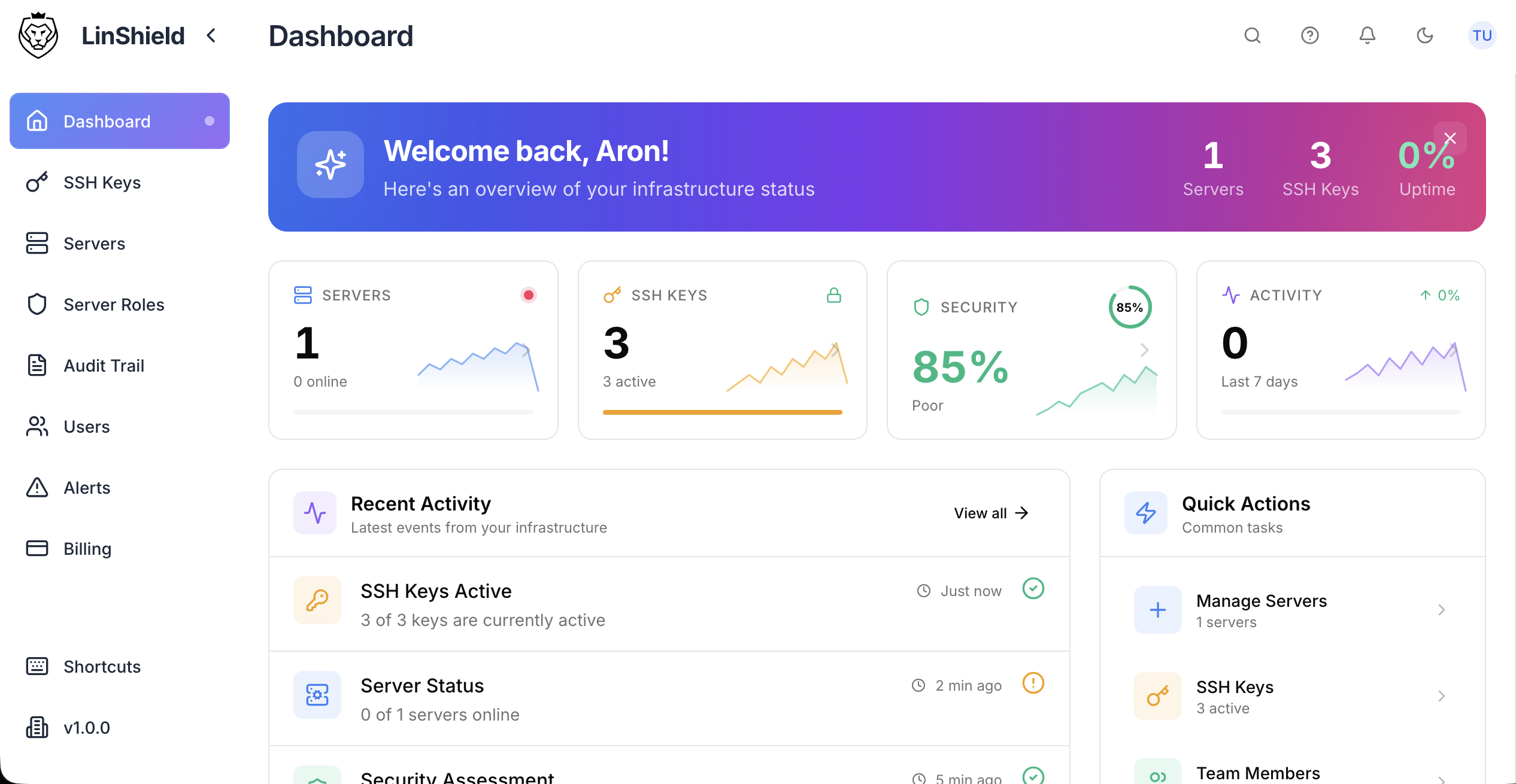
Take complete control of your Linux servers. Manage access, monitor activity, deploy software, and stay compliant - all from one intuitive dashboard.

Comprehensive security tools designed for modern infrastructure teams.
Lightweight daemon that runs on your servers. Real-time monitoring, package management, and secure communication via mTLS.
Learn MoreDeploy and manage application roles like NGINX, MySQL, Redis, and more with pre-built templates and one-click operations.
Learn MoreZero-knowledge key storage with 3-shard Threshold Secret Sharing. Your keys are never stored in a single location.
Learn MoreMulti-tenant architecture with complete data isolation. Manage teams, invite users, and control access seamlessly.
Learn MoreEvery action logged with timestamps, IP addresses, and user attribution. Immutable logs for complete accountability.
Learn MoreBuilt-in support for SOC 2, ISO 27001, GDPR, HIPAA, and PCI DSS. Generate compliance reports with one click.
Learn MoreSimple deployment, powerful protection.
Deploy our lightweight agent on your Linux servers with a single command. Works seamlessly across all major distributions.
$ curl -sSL https://app.linshield.com | bash
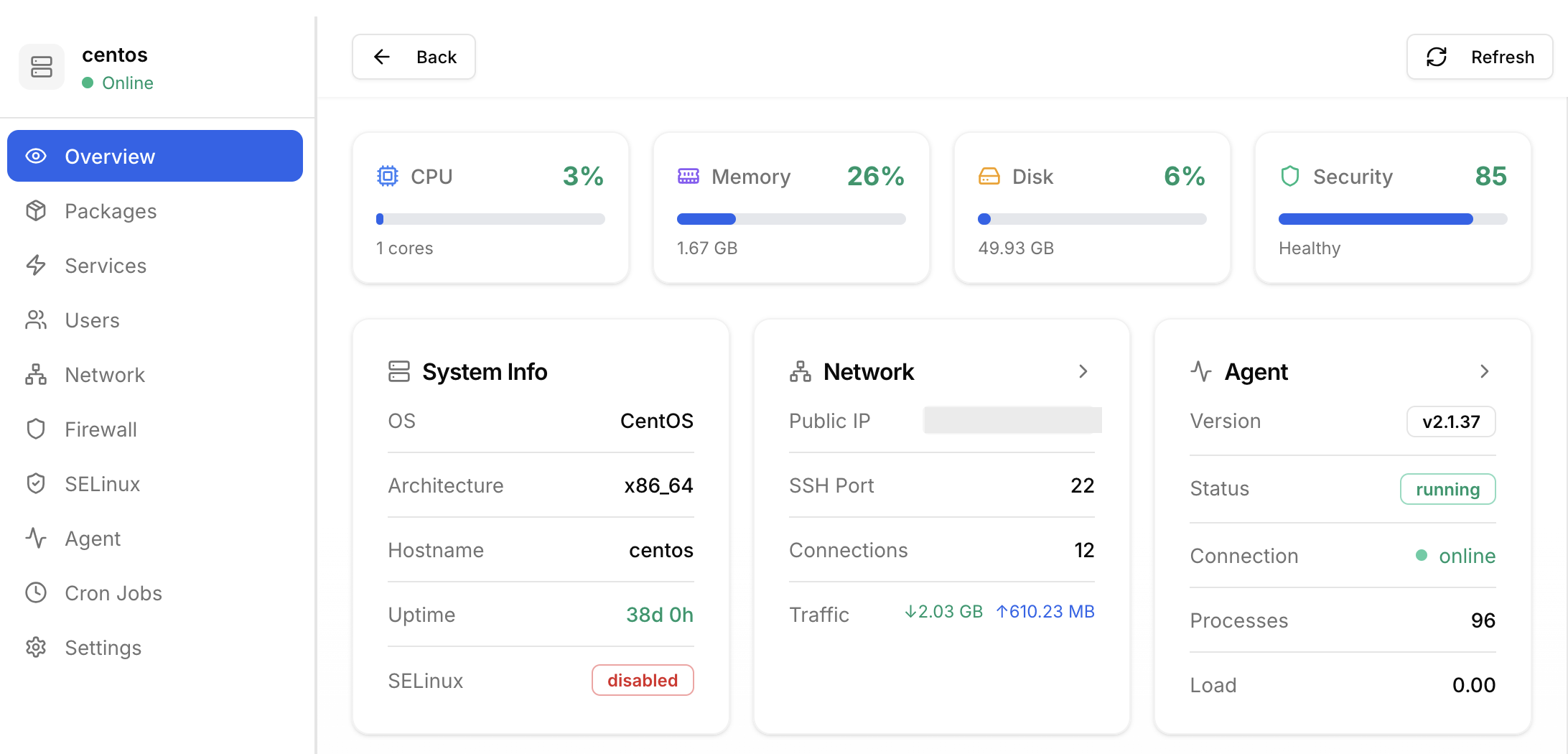
Gain complete visibility into your infrastructure. Monitor server health, manage packages, and respond to security events in real-time.
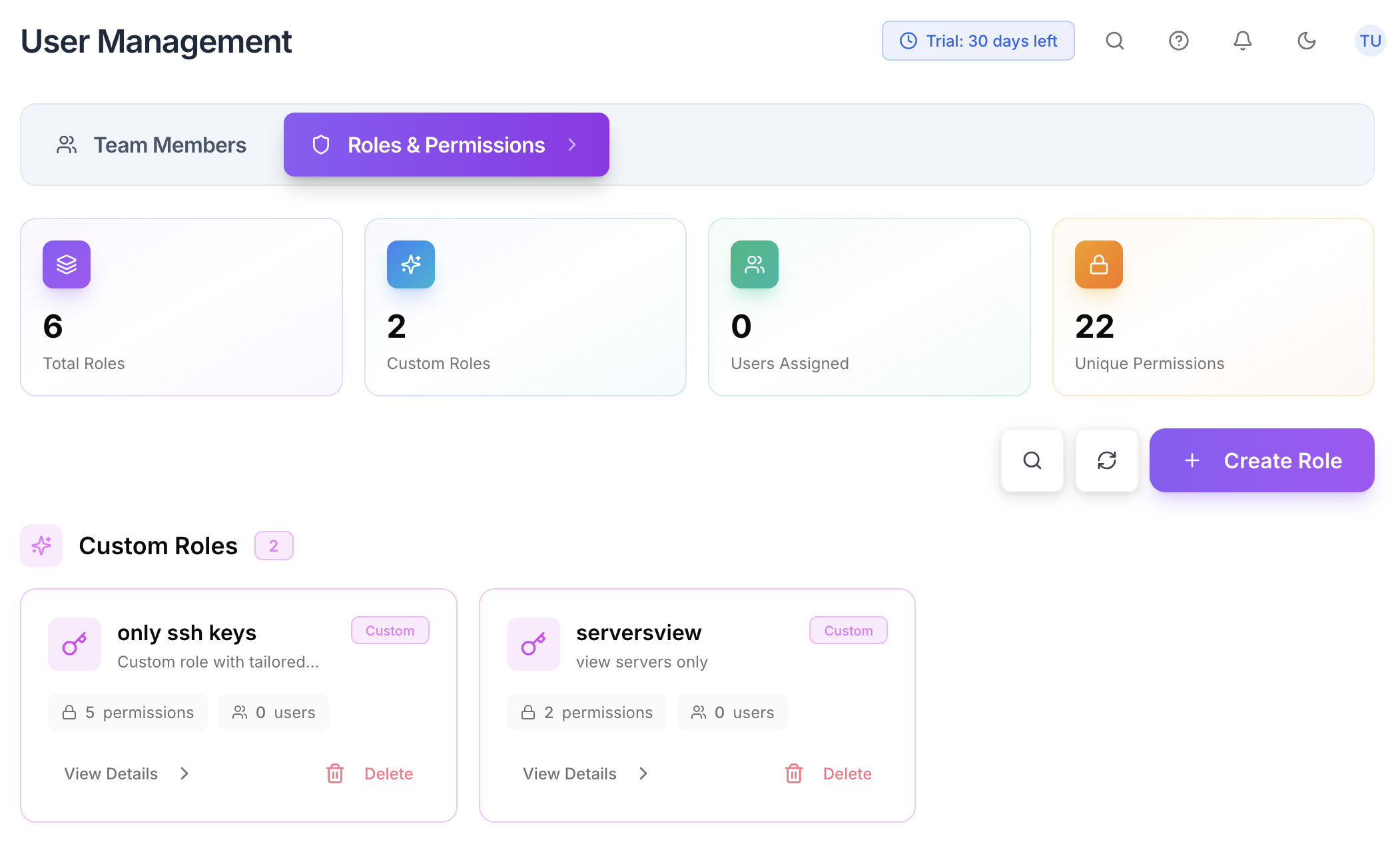
Set up your team with role-based permissions. Define who can access which servers and what actions they can perform.
Start your free trial today. No credit card required.